↗ OpenReview ↗ NeurIPS Homepage ↗ Chat
TL;DR#
3D Gaussian Splatting (3DGS) has become a popular method for 3D rendering, but the lack of effective copyright protection for 3D assets is a significant issue. Classical 3D steganography methods are not suitable for 3DGS because of its explicit 3D representation and real-time rendering speed. Previous methods that try to modify 3DGS either compromised rendering quality or were insecure.
This paper introduces GS-Hider, a new steganography framework designed specifically for 3DGS. GS-Hider uses a coupled secured feature attribute to replace the original spherical harmonics coefficients, creating a robust system that hides both images and 3D scenes while preserving rendering quality. The use of a coupled feature with parallel scene and message decoders ensures both high security and high fidelity. Extensive experiments demonstrate GS-Hider’s effectiveness in various scenarios.
Key Takeaways#
Why does it matter?#
This paper is crucial for researchers in 3D graphics and computer vision because it introduces a novel, robust framework for hiding information in 3D Gaussian Splatting (3DGS) point clouds. This addresses a critical need for copyright protection and secure communication in the increasingly prevalent field of real-time 3D rendering. The findings open avenues for further research into high-capacity, secure, and flexible steganography methods tailored to explicit 3D representations.
Visual Insights#

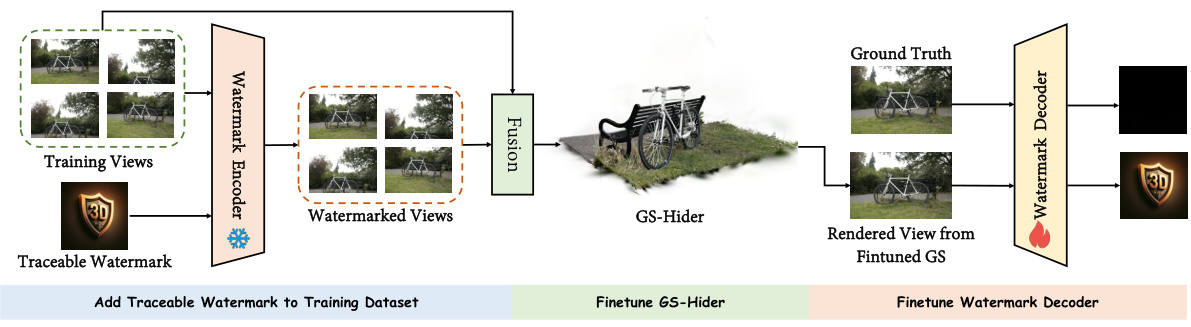
This figure illustrates the application scenario of the proposed GS-Hider steganography framework. Alice, the 3DGS trainer, uses training views of both the original and a hidden 3D scene to train the GS-Hider model. The model then produces a 3DGS point cloud file, a scene decoder (publicly available), and a message decoder (private). Alice uploads the point cloud file and scene decoder. Bob, a 3DGS user, can render the original 3D scene from the publicly available files. However, only Alice, possessing the private message decoder, can extract the hidden 3D scene, thus enabling copyright protection or secure communication.
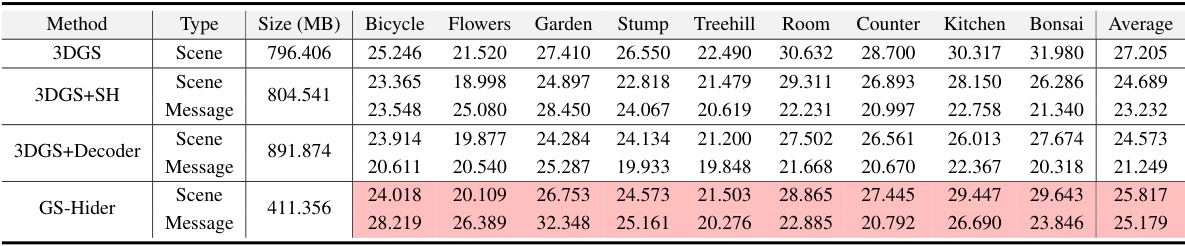
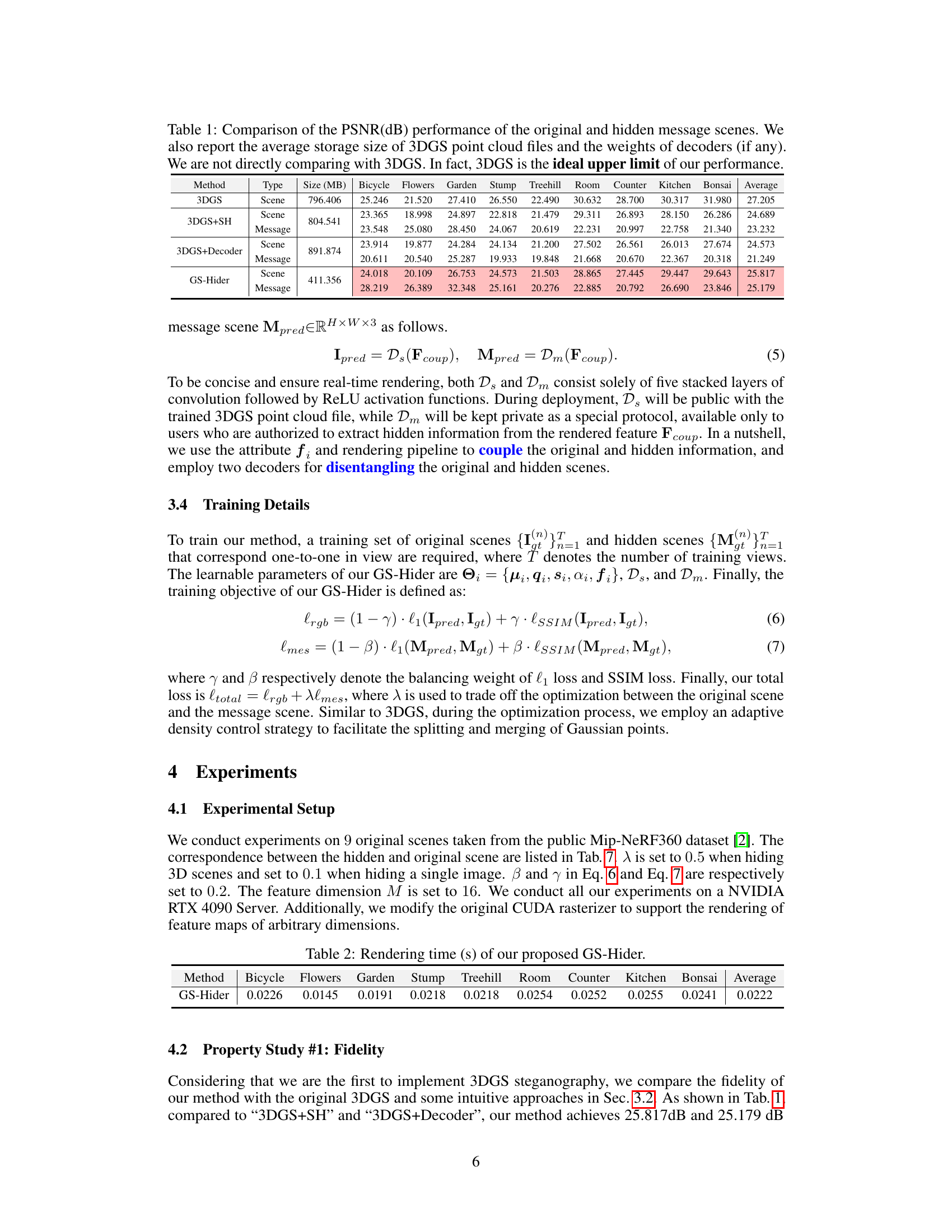
This table compares the Peak Signal-to-Noise Ratio (PSNR) in dB for original and hidden scenes using different methods: 3DGS, 3DGS+SH, 3DGS+Decoder, and GS-Hider. It also shows the average storage size (in MB) for each method and the size of the decoder weights (if applicable). The results show that GS-Hider achieves high PSNR for both original and hidden scenes while maintaining a relatively small file size.
In-depth insights#
3DGS Steganography#
3DGS steganography, a novel approach to data hiding, leverages the unique properties of 3D Gaussian Splatting (3DGS) for embedding information within 3D scene representations. Unlike previous methods which often target implicit representations or simple modifications to explicit ones, 3DGS steganography must contend with the explicit nature of the 3D point cloud and its real-time renderability. This requires carefully designed techniques to avoid impacting the rendering quality or introducing obvious artifacts. The core challenge is to find ways to modify 3DGS parameters, such as spherical harmonics coefficients or Gaussian distributions, that subtly encode data while preserving visual fidelity. Security is paramount, as the transparency of the 3DGS format necessitates robust techniques to prevent unauthorized extraction of the hidden information. The successful implementation of 3DGS steganography requires a balance between capacity, security, robustness, and fidelity, which presents a significant research opportunity.
GS-Hider Framework#
The GS-Hider framework presents a novel approach to steganography within the context of 3D Gaussian Splatting (3DGS). It cleverly addresses the challenges posed by the explicit and transparent nature of 3DGS data, where each point carries clear physical meaning, unlike implicit representations like NeRF. GS-Hider’s core innovation lies in the introduction of a ‘coupled secured feature attribute’. This attribute replaces the original spherical harmonics coefficients, allowing for the simultaneous encoding of both the original scene and a hidden message (multimodal messages such as 3D scenes and images are supported). The use of separate scene and message decoders is crucial, enabling the disentanglement of the original and hidden information without compromising rendering quality or security. The framework demonstrates exceptional security, robustness, and capacity, effectively hiding multi-modal data while maintaining high fidelity. The dual-decoder architecture contributes significantly to the security, making it difficult for unauthorized users to access the hidden information.
Security and Fidelity#
Achieving both high security and high fidelity in a steganography system is a significant challenge. Security focuses on preventing unauthorized access to the hidden message; strong encryption and robust embedding techniques are crucial. Fidelity, on the other hand, centers on preserving the quality of the cover media (in this case, the 3D model) after the secret message is embedded; imperceptible changes are vital. The interplay between these two is complex; strong security measures might compromise fidelity, and conversely, prioritizing fidelity could weaken security. A successful approach requires a careful balancing act. This balance is often achieved through sophisticated algorithms and careful selection of embedding locations within the 3D model. For example, modifying less visually salient features or using techniques that are resistant to common attacks is beneficial. Evaluation often involves quantitative metrics (e.g., PSNR for fidelity, detection rate for security) and qualitative assessments to ensure the trade-off is acceptable. Ultimately, the effectiveness of any steganographic method hinges on the specific context and the relative importance of security vs. fidelity.
Capacity and Versatility#
The capacity and versatility of a steganography method are crucial for practical applications. High capacity allows embedding substantial amounts of information, increasing the potential for data hiding. Versatility refers to the method’s ability to handle diverse data types (images, 3D scenes, audio, etc.) and conceal information in various media formats. A versatile method also adapts to different application scenarios, offering flexibility in the types of messages hidden and the ways they are extracted. The combination of high capacity and versatility makes a steganography system more robust and adaptable, capable of addressing diverse security and data-hiding needs in various contexts. Robustness against attacks is essential; a system with high capacity and versatility is valuable only if it can withstand attempts to detect or remove the hidden information.
Future Enhancements#
Future enhancements for this 3D Gaussian Splatting (3DGS) steganography method, GS-Hider, could significantly improve its capabilities. Improving rendering quality is crucial, potentially by integrating with advanced rendering techniques like Mip-Splatting to reduce artifacts and increase visual fidelity. This would enhance the imperceptibility of hidden messages. Efficiency enhancements are also key; the current system’s rendering speed is slower than the original 3DGS. Optimizations like pruning Gaussian points, reducing feature dimension, or refining network architectures could address this. Further research should explore security against more sophisticated attacks, and the robustness of the system under various conditions. Expanding the range of hidden data types beyond 3D scenes and images is another avenue of improvement, potentially incorporating multimodal data. Finally, developing a more user-friendly interface and providing clear guidelines would enhance practicality and accessibility, increasing GS-Hider’s adoption and impact. Expanding the research to other implicit 3D representations, such as NeRF, would also be valuable to test the generality of the method.
More visual insights#
More on figures
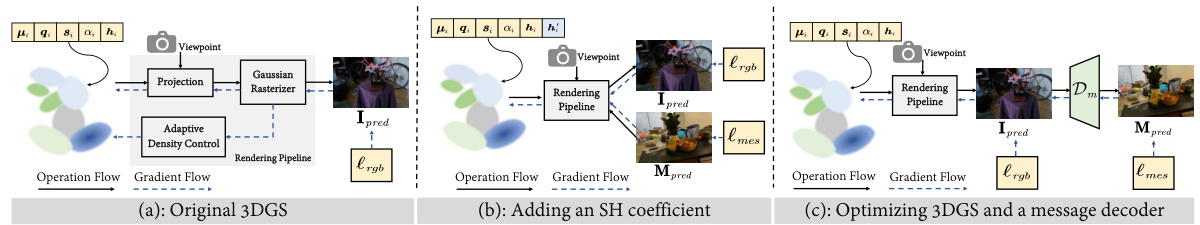
This figure compares three different approaches to 3D Gaussian Splatting (3DGS) steganography. (a) shows the original 3DGS pipeline. (b) demonstrates a naive approach of adding a spherical harmonic (SH) coefficient to embed information, which is insecure as the added coefficient is easily detectable. (c) illustrates another naive approach of jointly optimizing the 3DGS and a separate message decoder, which may compromise the original scene’s fidelity. The figure highlights that these intuitive methods are unsuitable for secure and high-fidelity 3DGS steganography.
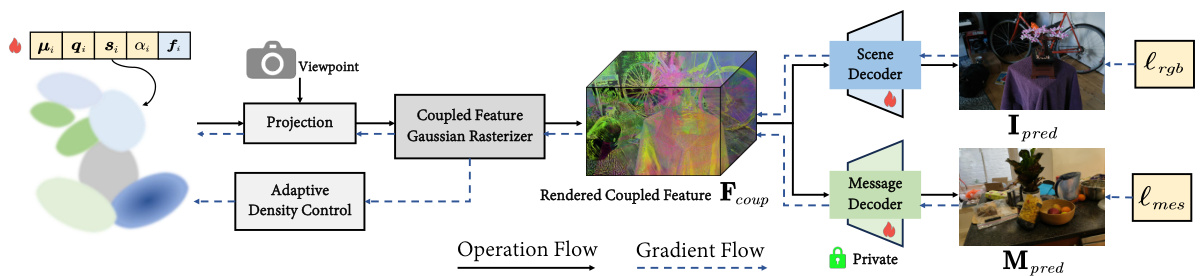
This figure illustrates the GS-Hider framework. It begins with the input of 3D Gaussian parameters (position μᵢ, opacity αᵢ, scaling factor sᵢ, rotation qᵢ, and coupled secured feature fᵢ). These parameters go through the projection, adaptive density control, and coupled feature Gaussian rasterizer stages. The resulting coupled feature Fcoup is then input to two parallel decoder networks: a scene decoder that outputs the rendered original RGB scene Ipred and a message decoder that outputs the hidden message Mpred. The message decoder’s output is private, protecting the hidden information.

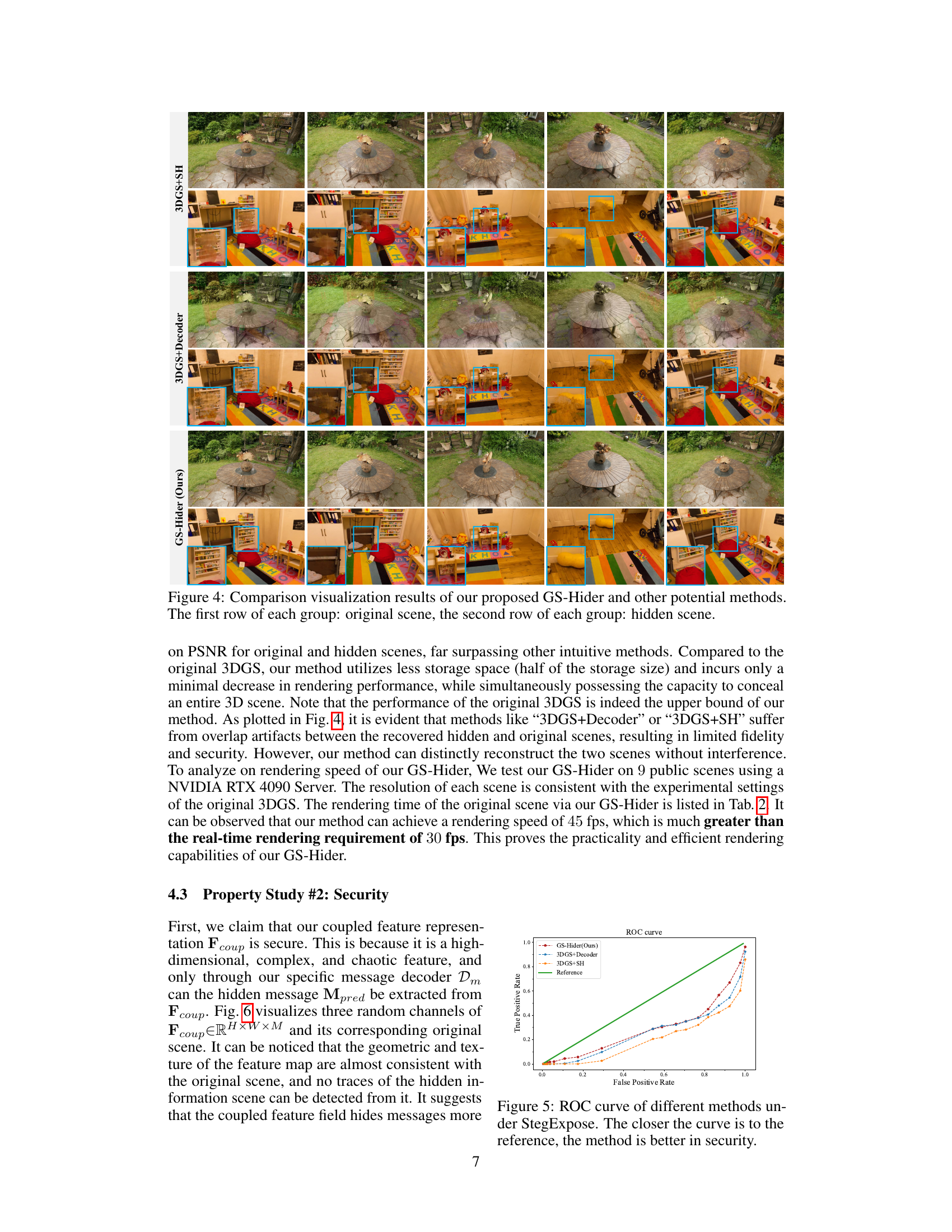
This figure compares the visual results of three different 3D scene steganography methods: GS-Hider (the proposed method), 3DGS+Decoder (optimizing 3DGS and a message decoder), and 3DGS+SH (adding an SH coefficient). Each group shows the original scene in the first row and the hidden scene in the second row, enabling a direct visual comparison. The figure highlights the superior quality and fidelity of the GS-Hider method in reconstructing both the original and hidden scenes without interference or artifacts.

This ROC curve illustrates the performance of GS-Hider and other comparative methods (3DGS+Decoder, 3DGS+SH) in terms of security against the StegExpose anti-steganography detector. A good method will have a curve that hugs the top-left corner, indicating high true positive rate (correctly identifying steganography) at low false positive rate (incorrectly flagging clean images). The reference line shows the expected performance of a random guess.
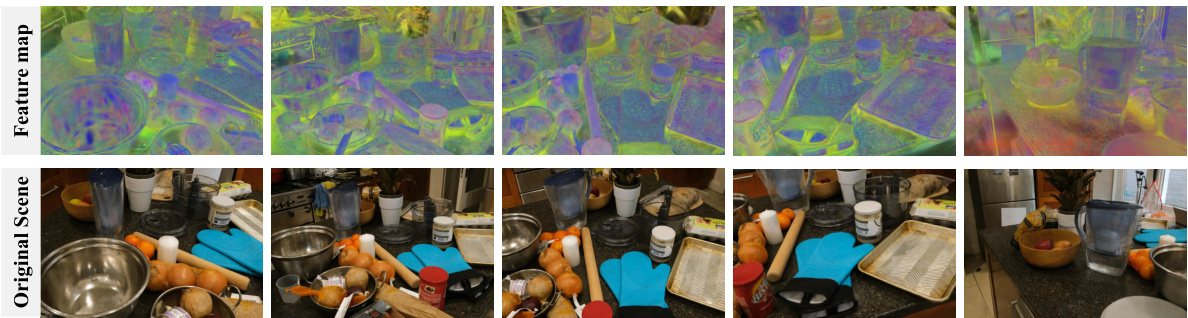
This figure visualizes a comparison between the rendered coupled feature map (Fcoup) and the rendering view of the original scene. The coupled feature map is a high-dimensional representation that integrates information from both the original and hidden scenes. The figure aims to demonstrate that the coupled feature map primarily retains the characteristics of the original scene, making it difficult to detect the presence of any hidden message. This is a key aspect of the GS-Hider’s security.

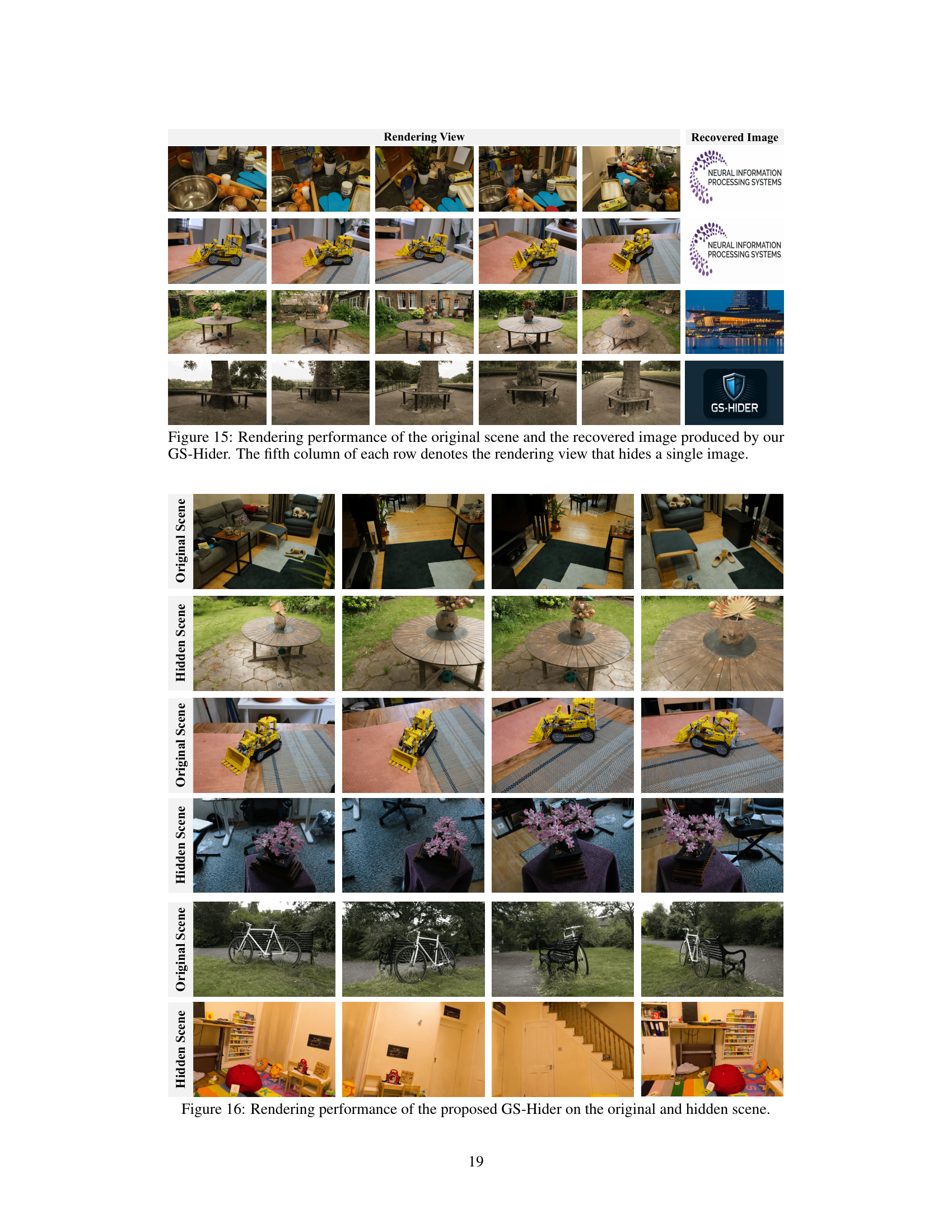
This figure compares the performance of GS-Hider and 3DGS+Decoder in single image hiding. The left columns show rendering views of the original scene. The right columns show the recovered hidden image, compared to the ground truth (GT). The fifth column in each row shows the specific viewpoint where the image is hidden. The results demonstrate that GS-Hider maintains a higher fidelity in the original scene while achieving comparable performance in recovering the hidden image compared to the baseline 3DGS+Decoder.

This figure shows the results of embedding multiple 3D scenes into a single original 3D scene using the proposed GS-Hider method. It demonstrates the ability of the method to hide more than one 3D scene simultaneously without significant visual artifacts or impact to the quality of the original scene. Each set of three images shows the original scene, followed by two different hidden scenes successfully embedded within it. This showcases the large capacity and versatility of the GS-Hider for multi-scene hiding applications.
This figure illustrates the framework of GS-Hider, a 3DGS steganography method. It shows how hidden information (3D scenes or images) is embedded into the original 3D scene using a coupled secured feature attribute. The coupled feature is processed by a rendering pipeline to generate a coupled feature map. This map is then fed to two decoders, one for reconstructing the original scene and another for extracting the hidden message.

This figure shows the results of attempting to decode a hidden scene using a randomly initialized message decoder. The top row displays the original scene, and the bottom row shows what the decoder produced. The significant difference demonstrates that a randomly initialized decoder cannot extract the hidden scene, highlighting the security of the GS-Hider method.

This figure shows the results of using a randomly initialized message decoder to try to reconstruct the hidden scene. The results demonstrate that the wrong decoder cannot reconstruct the hidden scene, highlighting the security of the proposed GS-Hider.
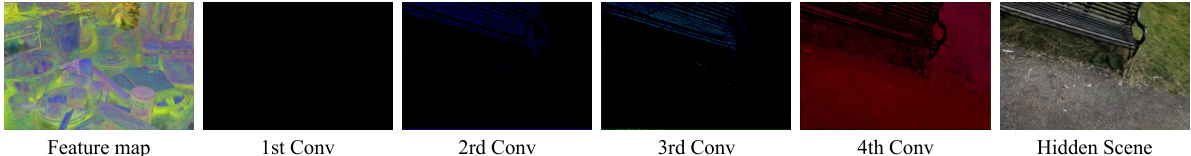
This figure visualizes the intermediate feature maps within the message decoder of the proposed GS-Hider model. Specifically, it shows three channels (14th, 15th, and 16th) of the feature maps at different stages of processing within the decoder. The figure aims to illustrate how the decoder progressively extracts and refines the hidden message from the coupled feature representation. By examining the feature maps at each convolutional layer, one can observe the transition from a complex and seemingly chaotic initial representation to the clear and coherent final representation of the hidden scene.
This figure shows the results of using a randomly initialized message decoder to try to reconstruct a hidden scene. It demonstrates that the decoder cannot reconstruct the scene, highlighting the security of the proposed GS-Hider method because the hidden information is not simply memorized by the decoder, but rather is extracted through a designed process that requires the correct decoder.

This figure compares the visualization results of the proposed GS-Hider method with two other potential methods for 3D scene steganography. The top row in each section shows views of the original scene, while the bottom row shows the corresponding extracted hidden scene. The figure demonstrates the superior fidelity and visual quality of GS-Hider compared to the alternative methods, which show noticeable artifacts and distortions in the reconstructed hidden scenes.
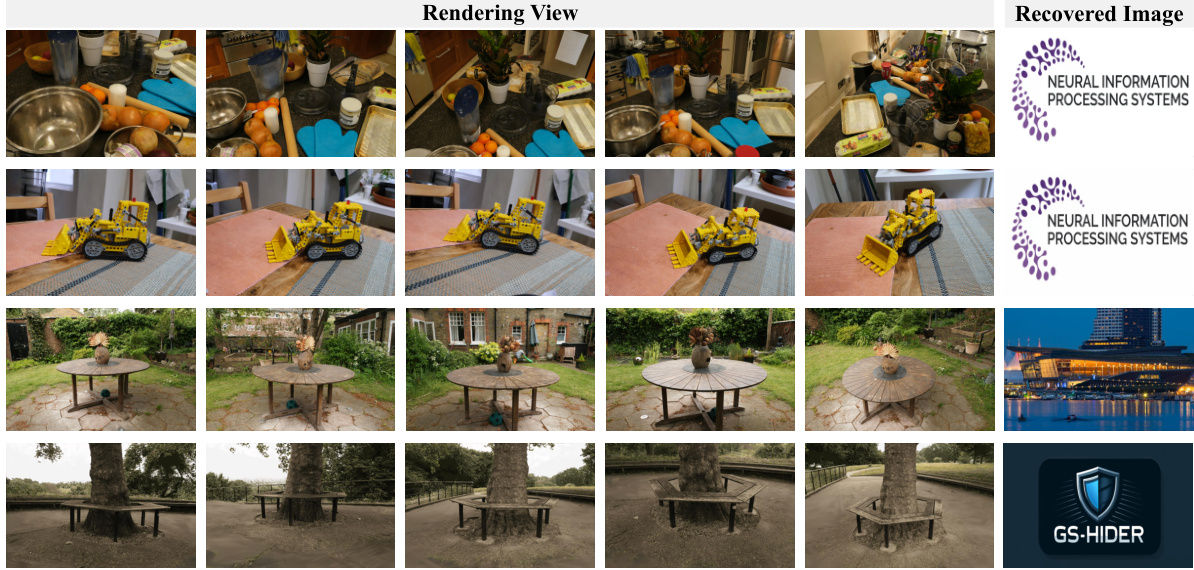
The figure demonstrates the capability of GS-Hider in hiding a single image within a 3D scene. It shows multiple rendering views of a scene, followed by the corresponding image recovered by the GS-Hider. The fifth column displays a specific viewpoint in which a single image was hidden. The high-fidelity reconstruction of the hidden image, as shown by the recovered image, demonstrates the efficacy of the proposed approach for image steganography in 3D scenes.

This figure compares the visualization results of the proposed GS-Hider method with two other potential steganography methods for 3D Gaussian splatting. It shows the original scene and the hidden scene generated by each method for several different example scenes. The comparison helps illustrate the superiority of GS-Hider in terms of the fidelity of the original scene and the quality of the hidden scene reconstruction.
More on tables

This table presents the rendering time in seconds for each of the nine scenes used in the GS-Hider experiments. The rendering times are broken down by scene (Bicycle, Flowers, Garden, Stump, Treehill, Room, Counter, Kitchen, Bonsai) and show the average rendering time across all scenes. The data reflects the efficiency of the GS-Hider algorithm in generating images in real-time.

This table presents the results of a robustness study on the GS-Hider method. Two pruning methods (sequential and random) were used to degrade the Gaussians in the 3D scene, and the impact on the fidelity of both the original and hidden scenes was evaluated using PSNR, SSIM, and LPIPS metrics. The results show that the GS-Hider method is robust to both sequential and random pruning, with minimal impact on the fidelity of both the original and hidden scenes, even with up to 25% of the Gaussians pruned.
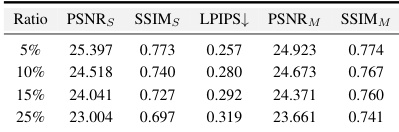
This table presents the robustness analysis of the proposed GS-Hider method under different pruning methods. It shows the performance (PSNR, SSIM, LPIPS) for both the original and hidden scenes with different ratios (5%, 10%, 15%, and 25%) of sequential and random pruning of Gaussians. This analysis evaluates how well the method maintains its fidelity and quality even when some Gaussian points are removed.

This ablation study investigates the effects of key hyperparameters on the performance of the GS-Hider. It shows the impact of balancing weight (λ), feature dimension (M), and the number of convolutional layers in the decoder networks on the fidelity of both the original and hidden scenes (measured using PSNR, SSIM, and LPIPS). The results help to determine optimal hyperparameter settings for the best balance between original scene fidelity and hidden message capacity and security.

This table presents the Peak Signal-to-Noise Ratio (PSNR) values for the original scene (PSNRs), hidden message (PSNRM), and watermarked image extracted from an arbitrary 2D RGB viewpoint (PSNRw). The results demonstrate the effectiveness of the GS-Hider method in extracting copyright information from limited viewpoints, even when the complete 3DGS point cloud file is unavailable. The PSNR values represent the fidelity of the image reconstruction compared to the original.

This table shows the correspondence between the original and hidden scenes used in the GS-Hider experiments. Note that for some scenes (Playroom and Bicycle), there are repeated entries because those scenes had fewer ‘illegal’ views. This ensured sufficient data for training the GS-Hider model.

This table presents the Peak Signal-to-Noise Ratio (PSNR), Structural Similarity Index (SSIM), and Learned Perceptual Image Patch Similarity (LPIPS) metrics for the original scenes rendered by the GS-Hider without any hidden message embedded. It shows the fidelity of the rendered original scenes, which is compared against the results with hidden messages in the paper.

This table presents a comparison of Peak Signal-to-Noise Ratio (PSNR) values for original and hidden message scenes, obtained using different methods. It also shows the average storage size of 3D Gaussian Splatting (3DGS) point cloud files and the decoder weights for each method. The table highlights that 3DGS represents the ideal upper limit of performance for the methods evaluated.
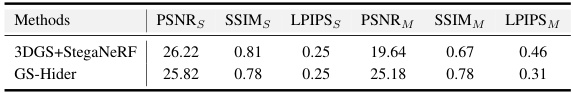
This table compares the performance of the proposed GS-Hider method with the 3DGS+StegaNeRF method. It shows a quantitative comparison of the Peak Signal-to-Noise Ratio (PSNR), Structural Similarity Index (SSIM), and Learned Perceptual Image Patch Similarity (LPIPS) metrics for both the original scene (S) and the hidden message (M). The results demonstrate the fidelity of the original scene and the quality of the hidden message produced by each method.
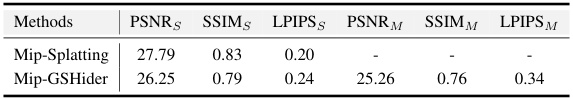
This table presents a comparison of rendering quality metrics between Mip-Splatting and Mip-GSHider. Mip-GSHider is an extension of the GS-Hider method to work with Mip-Splatting. The metrics shown are PSNR, SSIM, and LPIPS for both the original scene (S) and the hidden message (M). The results demonstrate that while incorporating the GS-Hider’s steganography capabilities into Mip-Splatting does reduce rendering quality, the fidelity of both the original and hidden scenes remains relatively high.
Full paper#