↗ OpenReview ↗ NeurIPS Homepage ↗ Chat
TL;DR#
Current watermarking methods for generative content struggle to balance robustness and concealment. They often rely on empirically injecting weak watermarks to maintain invisibility, compromising security. This creates a need for techniques that actively hide stronger watermarks without sacrificing invisibility.
ROBIN tackles this by explicitly embedding a robust watermark into an intermediate stage of the diffusion process. It then leverages adversarial optimization to craft a prompt that guides the model to seamlessly conceal the watermark in the final image. This approach enables the use of stronger, more robust watermarks that are still highly imperceptible. Experiments showcase ROBIN’s superior performance in invisibility and resistance to image manipulations compared to existing methods.
Key Takeaways#
Why does it matter?#
This paper is crucial for researchers working on watermarking techniques for generative models, particularly diffusion models. It addresses the critical challenge of balancing robustness and invisibility in watermarks, offering a novel solution with significant implications for intellectual property protection and content authenticity in the age of AI-generated content. The adversarial optimization approach provides a valuable framework for future research on robust and imperceptible watermarking techniques, paving the way for more secure and reliable content verification.
Visual Insights#
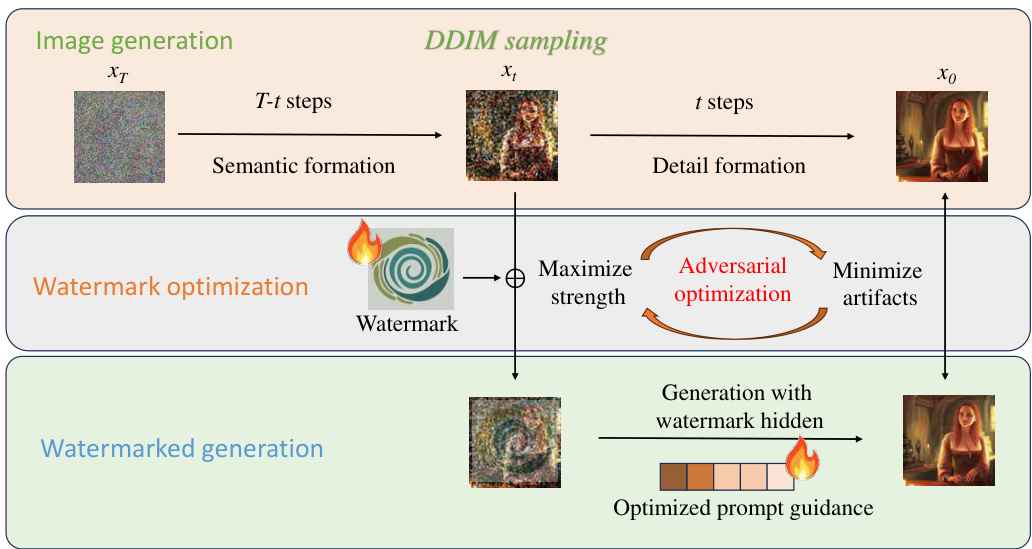
The figure illustrates the ROBIN watermarking process. It shows three main stages: 1. Watermark Optimization: A robust watermark is generated (optimized for strength), and simultaneously an adversarial optimization process generates an optimized prompt signal that will later be used to hide the watermark in the generated image (optimized to minimize artifacts). 2. Watermark Implantation: The robust watermark is embedded at an intermediate stage in the image generation process, somewhere between the semantic and detail formation stages. 3. Watermarked Generation: The image generation process continues. The optimized prompt guides the model, successfully hiding the watermark within the final generated image.
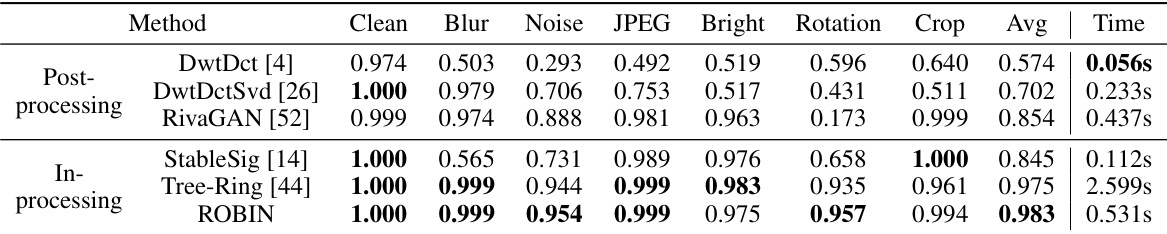
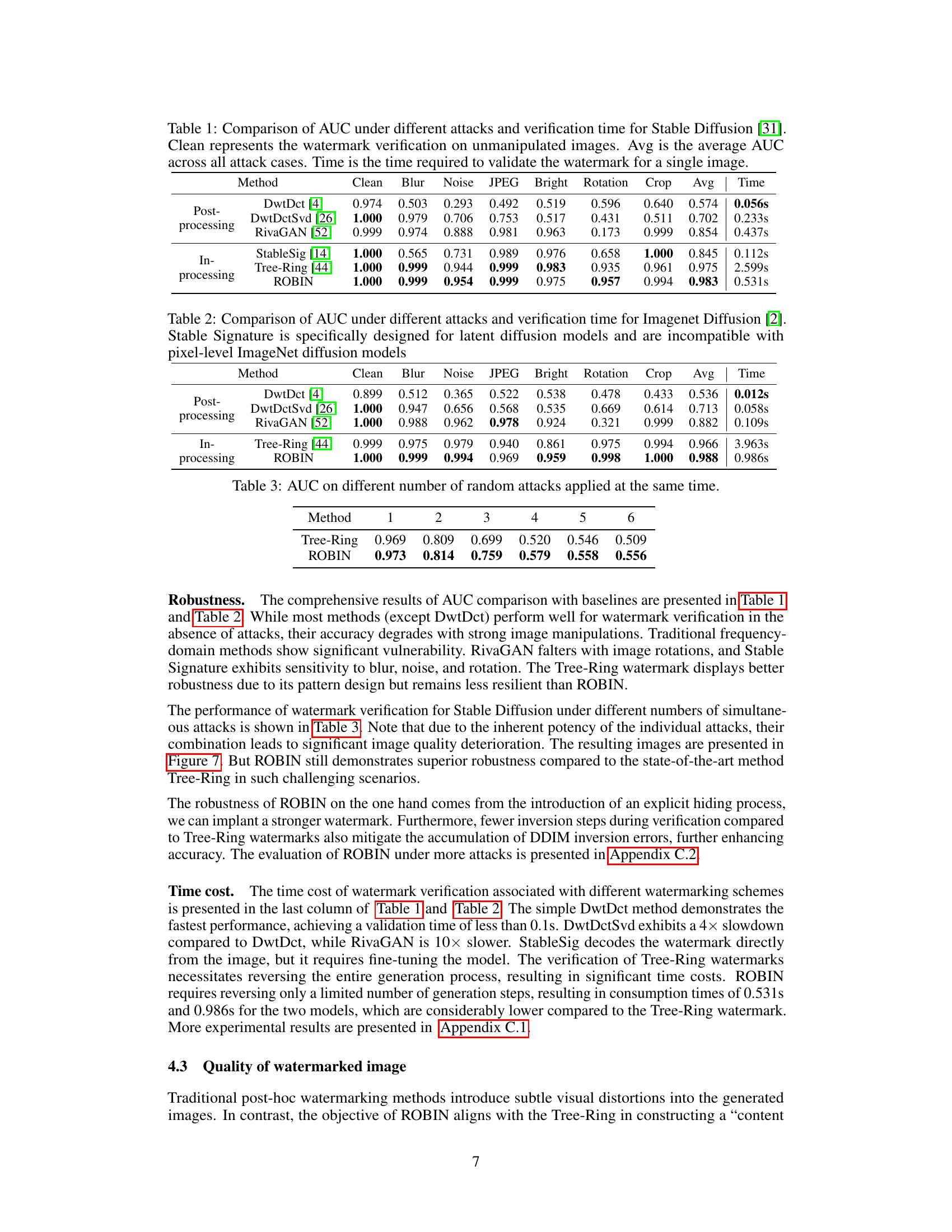
This table compares the performance of different watermarking methods (DwtDct, DwtDctSvd, RivaGAN, StableSig, Tree-Ring, and ROBIN) on Stable Diffusion images under various attacks (blur, noise, JPEG compression, brightness changes, rotation, and cropping). It shows the Area Under the ROC Curve (AUC) for watermark verification, averaged across all attacks, and the average time taken for verification. A higher AUC indicates better watermark detection performance. The ‘Clean’ column shows the AUC for unattacked images. The table highlights ROBIN’s superior performance in terms of both AUC and verification time.
In-depth insights#
Adversarial Hiding#
The concept of “Adversarial Hiding” in the context of watermarking generative models introduces a novel approach to concealing watermarks. Instead of passively embedding a watermark with limited strength to maintain invisibility, this technique actively employs adversarial optimization. This process pits two networks against each other: one to maximize watermark robustness, and another to minimize its detectability within the final generated image. The adversarial nature of this approach is key, enabling the embedding of stronger watermarks that would otherwise be too visible. The embedding process often involves injecting the watermark at an intermediate stage of the generative process and then using adversarial training to guide the model towards effectively concealing it. This active concealment dramatically alters the trade-off between robustness and invisibility, paving the way for more secure watermarks. Such a system likely involves carefully selected loss functions to balance fidelity of the generated image with the strength of the hidden watermark, creating a more robust and sophisticated method for protecting digital ownership and authenticity.
Watermark Robustness#
Watermark robustness, a crucial aspect of any watermarking scheme, assesses its resilience against various attacks and manipulations. A robust watermark remains detectable even after significant image alterations, such as compression, geometric transformations (cropping, scaling, rotation), or noise addition. The paper’s approach, focusing on embedding robust watermarks in an intermediate diffusion state and then guiding the model to conceal them actively through adversarial optimization, is a promising strategy for achieving high robustness. This method actively addresses the common trade-off between invisibility and robustness found in traditional methods, which typically compromise robustness to enhance invisibility. The results demonstrate the method’s superior robustness against various attacks, including those involving combinations of multiple image manipulations, confirming the effectiveness of the proposed active concealment strategy. The strength of the watermark plays a vital role in robustness, but it is carefully balanced against the need for imperceptibility to avoid visible artifacts in the final image. Further research could explore the theoretical limits of watermark strength while maintaining invisibility and the robustness against more sophisticated, targeted attacks aimed at specifically removing the watermark.
Diffusion Model Choice#
The choice of diffusion model significantly impacts the performance and characteristics of watermarking. Factors to consider include the model’s architecture (latent vs. image diffusion), its training data, and its inherent ability to handle noise and perturbations. Latent diffusion models, operating in a compressed latent space, offer computational advantages but might introduce artifacts during inversion, impacting invisibility and robustness. Image diffusion models, processing the image directly, preserve finer details but are computationally more intensive. The training data’s diversity is crucial; models trained on diverse datasets yield watermarks that are more robust to tampering and better generalize across various image styles. Finally, a diffusion model’s noise-handling properties are directly related to watermark resilience. A model that gracefully manages noise during the forward diffusion process will likely produce less noticeable artifacts when the watermark is embedded and better withstand various image manipulations during the watermark verification stage. The optimal model should balance invisibility, robustness, and computational efficiency based on the application’s specific needs.
Implantation Point#
The optimal point for watermark implantation in the diffusion process is crucial for balancing invisibility and robustness. Early implantation might disrupt semantic formation, impacting image quality, while late implantation could leave the watermark visible due to insufficient hiding space. The authors demonstrate that an intermediate stage, specifically between steps 200 and 300, provides the best compromise. This optimal point allows for the watermark’s embedding without significantly altering the image content’s semantics or introducing noticeable visual artifacts. Frequency domain implantation further enhances robustness against typical image manipulations. Adversarial optimization of the watermark and prompt guidance is key to minimizing visible artifacts. The selection of this implantation point is supported by experiments showcasing a superior balance between robustness and invisibility compared to alternative strategies.
Future Work#
The paper’s ‘Future Work’ section would ideally delve into several promising directions. Improving the watermark’s robustness against more sophisticated attacks is crucial; exploring advanced adversarial training techniques or incorporating perceptual hashing could significantly enhance resilience. Investigating alternative watermark embedding strategies, such as exploring different points within the diffusion process or employing different frequency domains, would be valuable. Further research into the invertibility of the diffusion process is warranted as it directly impacts watermark verification reliability. A promising area is exploring the use of other diffusion models and architectures beyond Stable Diffusion to assess generalizability and performance. Analyzing the impact of different prompt engineering techniques on watermark invisibility and robustness is also key. Finally, a comprehensive study on the trade-offs between watermark strength, invisibility, and verification speed would provide a more holistic understanding of ROBIN’s capabilities and limitations.
More visual insights#
More on figures
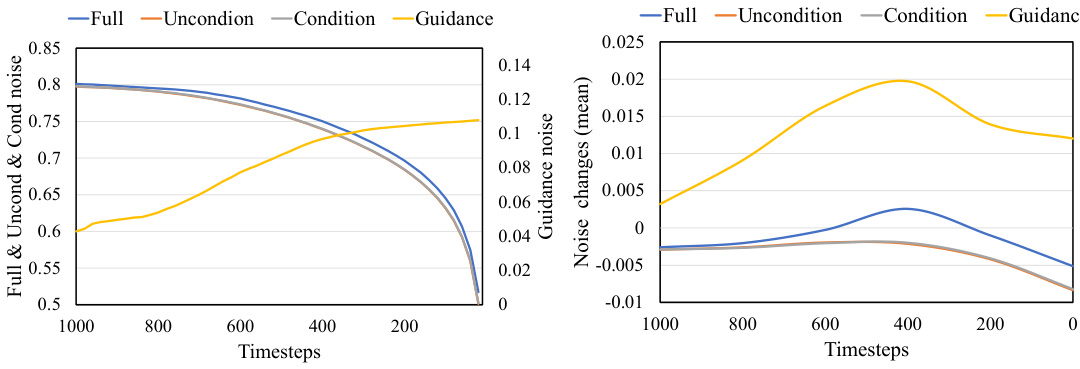
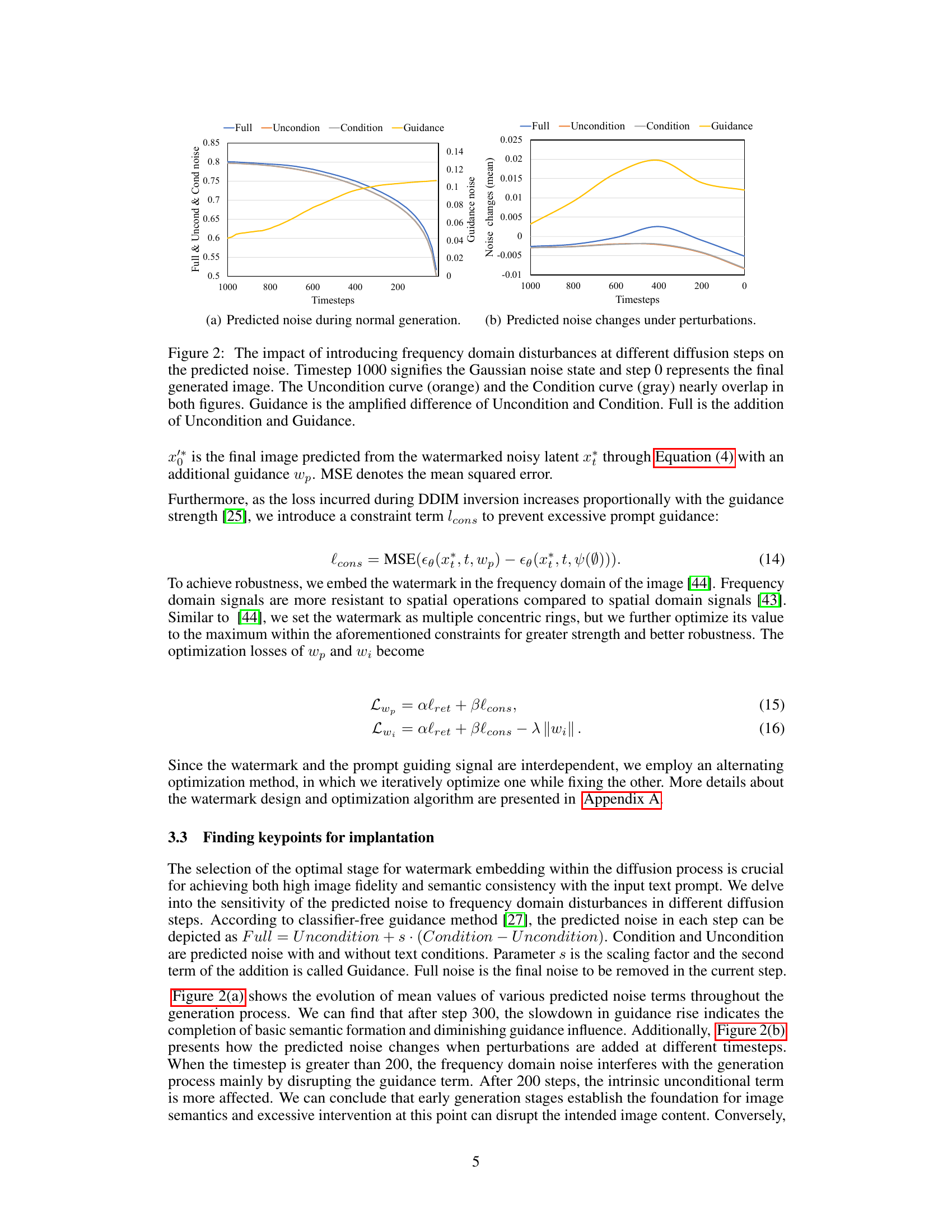
This figure shows how introducing frequency domain disturbances at various diffusion steps affects the predicted noise during image generation. It compares the predicted noise under different conditions: normal generation, only using text conditions, and combining text conditions with additional guidance. The results highlight the impact of the additional prompt guidance on noise prediction during different stages of the diffusion process.

This figure shows three example images generated by Stable Diffusion model using three different methods: without watermark, with Tree-Ring watermark, and with ROBIN watermark. For each image, three versions are presented side-by-side. The prompts used for generating the images are also listed above each set of three images. The figure demonstrates that ROBIN can generate images that are very similar to the original images without watermarks, while Tree-Ring approach produces images that are quite different. This is because ROBIN uses an explicit watermark hiding process that minimizes artifacts and preserves image quality, while Tree-Ring modifies the semantics of the original image.

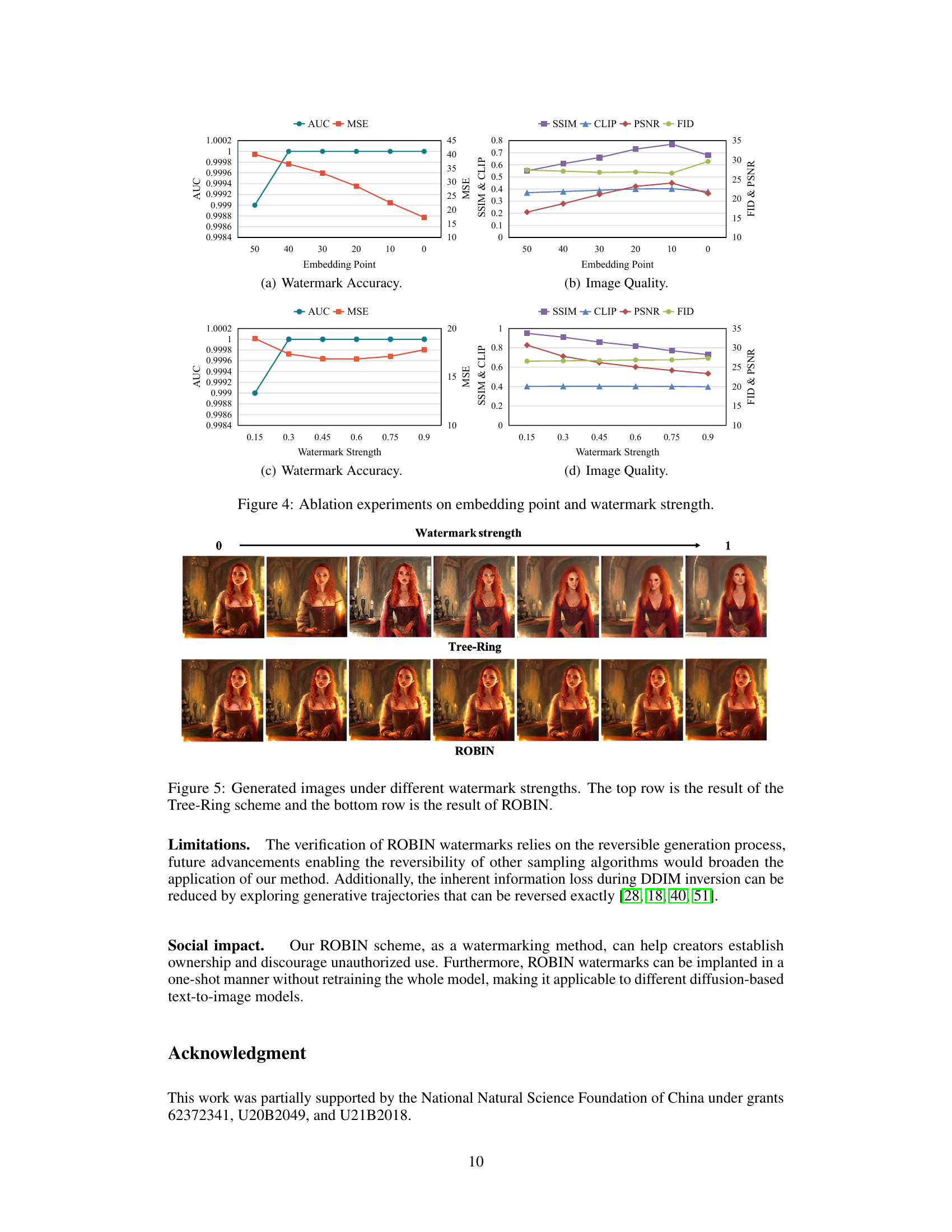
This figure presents the results of ablation studies on two key hyperparameters of the ROBIN watermarking method: the embedding point (the diffusion step at which the watermark is embedded) and the watermark strength. Subfigures (a) and (c) show the watermark accuracy (AUC and MSE) across different embedding points and watermark strengths respectively. Subfigures (b) and (d) show image quality metrics (PSNR, SSIM, CLIP, and FID) for the same parameter variations. The results demonstrate the impact of these choices on both watermark robustness and the quality of the generated watermarked image, helping to optimize the ROBIN system for invisibility and robustness.
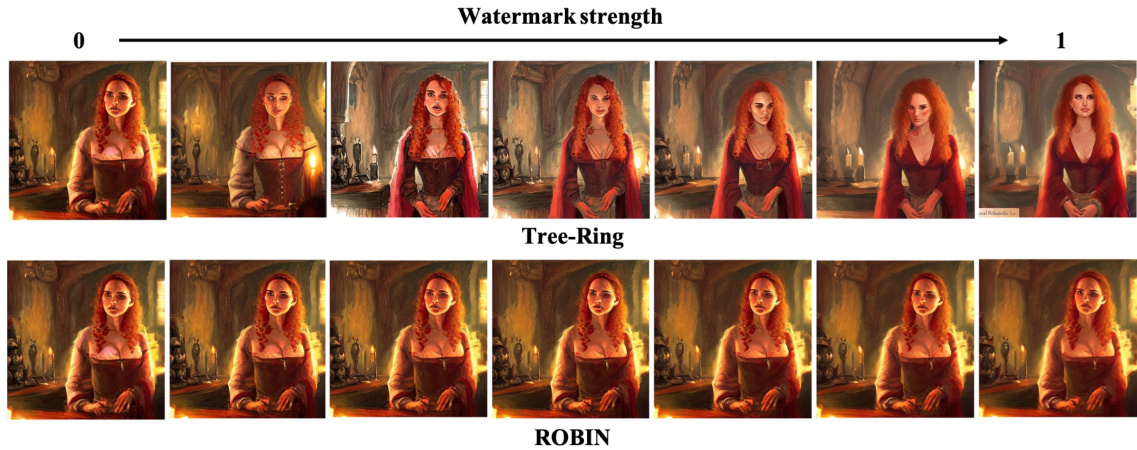
This figure shows a comparison of images generated with varying watermark strengths using the Tree-Ring and ROBIN methods. The top row displays images generated by the Tree-Ring approach, while the bottom row shows images from the ROBIN approach. Each row contains a series of images, progressing from a low watermark strength (left side) to a high watermark strength (right side), illustrating the impact of watermark strength on image quality and visual artifacts for both methods.

This figure shows the robustness of ROBIN’s watermark against various image manipulations. The original image is shown on the far left, followed by the same image subjected to blurring, adding noise, JPEG compression, brightness adjustments, rotation, and cropping. The watermark is designed to remain verifiable even under these transformations.

This figure shows the results of applying various image manipulations (Gaussian blur, JPEG compression, color jitter, random cropping, and rotation) with increasing combinations. It demonstrates the robustness of the watermarking method under multiple attacks simultaneously.

This figure shows three sets of images generated by Stable Diffusion and Imagenet Diffusion models using three different prompts: ‘Young, curly haired redhead girl in a dark medieval inn’, ‘Full body portrait of white haired girl in spider man suit’, and ‘Cloudscape, nebula gasses in the background, fantasy magic angel’. Each set includes an image generated without a watermark (W/o Watermark), an image watermarked with the Tree-Ring method, and an image watermarked with the ROBIN method. The images demonstrate the ability of ROBIN to preserve the image quality and semantic content of the generated images while still embedding a watermark.

This figure shows a qualitative comparison of images generated by three different methods: without watermarking, using the Tree-Ring watermarking method, and using the ROBIN watermarking method. Each method is applied to three different text prompts, resulting in three sets of images for comparison. The figure highlights the visual differences between the approaches, showing how the ROBIN method aims for less visible alteration of the generated image compared to Tree-Ring. This demonstrates the different approaches to balancing invisibility and robustness in watermarking diffusion models.

This figure shows a comparison of images generated using three different methods: without a watermark, with a Tree-Ring watermark, and with a ROBIN watermark. The goal is to visually demonstrate the invisibility of the watermarks embedded by each method. Each row represents the results for a different text prompt. The figure showcases that the ROBIN method produces images that are visually very similar to the images generated without any watermark, indicating successful watermark embedding without visual artifacts, unlike the Tree-Ring approach.

This figure shows a qualitative comparison of images generated by three different methods: without watermark, with Tree-Ring watermark, and with ROBIN watermark. For each method, several images are shown corresponding to different text prompts. The goal is to visually demonstrate the impact of each watermarking technique on the generated image quality and semantic coherence with the given prompt.

The figure illustrates the ROBIN watermarking process. A robust watermark is embedded in a middle stage of the image generation process. An adversarial optimization algorithm then generates an optimal prompt signal to guide the diffusion model and hide the watermark without noticeably affecting the final generated image. This approach balances robustness (the watermark’s ability to survive image manipulations) and invisibility (the watermark’s imperceptibility to the human eye).
More on tables
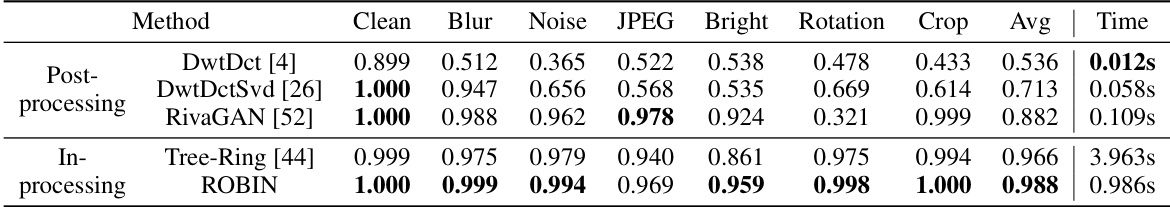
This table compares the performance of different watermarking methods (DwtDct, DwtDctSvd, RivaGAN, Tree-Ring, and ROBIN) on the ImageNet Diffusion model [2] in terms of Area Under the ROC Curve (AUC) and verification time under various attacks (Blur, Noise, JPEG compression, Brightness changes, Rotation, and Cropping). It highlights the robustness and efficiency of the ROBIN method compared to others.

This table shows the Area Under the ROC Curve (AUC) values for the Tree-Ring and ROBIN watermarking methods under varying numbers of simultaneous attacks. It demonstrates the robustness of each method against multiple image manipulations (blurring, noise, JPEG compression, brightness adjustments, rotation, and cropping). Higher AUC values indicate better watermark verification accuracy. The results show that ROBIN maintains superior robustness compared to Tree-Ring, especially when multiple attacks are combined.
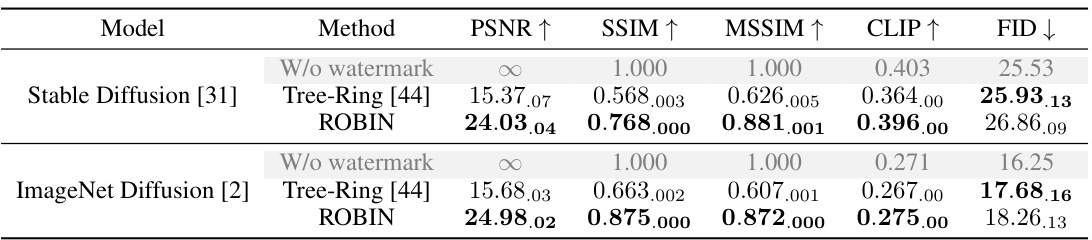
This table presents a quantitative comparison of the image quality between watermarked and unwatermarked images generated by different methods. It uses several metrics to assess quality: PSNR (Peak Signal-to-Noise Ratio), SSIM (Structural Similarity Index), MSSIM (Multiscale Structural Similarity Index), CLIP (a metric assessing alignment between image and text description), and FID (Fréchet Inception Distance, measuring the similarity of image distributions). The results are averaged over five independent runs to account for variability. The table helps to understand the impact of watermarking techniques on the generated image quality and semantic alignment with the text prompt.

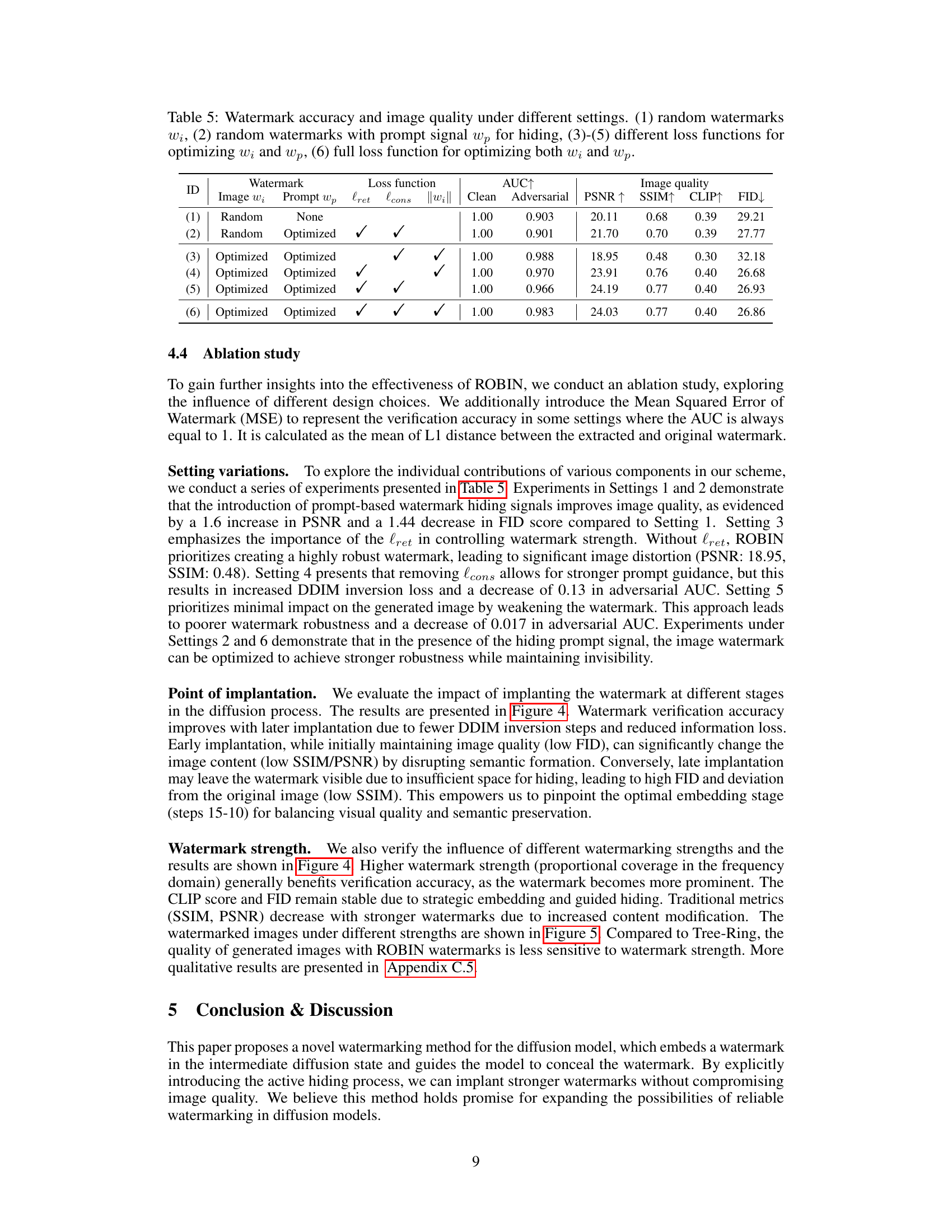
This table presents the ablation study results, showing the effects of different settings on watermark accuracy and image quality. It compares the performance using random watermarks, optimized watermarks with and without a prompt for hiding, and various combinations of loss functions. The metrics used are AUC (Area Under the ROC Curve) for accuracy, PSNR (Peak Signal-to-Noise Ratio), SSIM (Structural Similarity Index), CLIP score (alignment with text prompt), and FID (Fréchet Inception Distance) for image quality.

This table compares the time taken for generation and validation of watermarks using different watermarking methods on Stable Diffusion and Imagenet Diffusion models. It shows the time cost for both the generation of watermarked images and the subsequent validation of the watermark. Post-processing methods generally have faster validation times compared to in-processing methods, which require reversing steps in the diffusion process. The results highlight the trade-off between watermarking approaches and the time required for verification.

This table presents the Area Under the Curve (AUC) for watermark verification using three different methods: Tree-Ring, and ROBIN. The AUC is calculated under reconstruction attacks using three different models: VAE-Bmshj2018, VAE-Cheng2020, and Diffusion model. The results show ROBIN outperforms Tree-Ring in all cases, demonstrating its superior robustness against reconstruction attacks.

This table presents the Area Under the ROC Curve (AUC) values for watermark verification on images generated from noise using a noise-to-image diffusion model. It shows the performance under various image manipulations, including blurring, adding noise, JPEG compression, brightness changes, rotation, and cropping. The average AUC across all manipulations is also given.
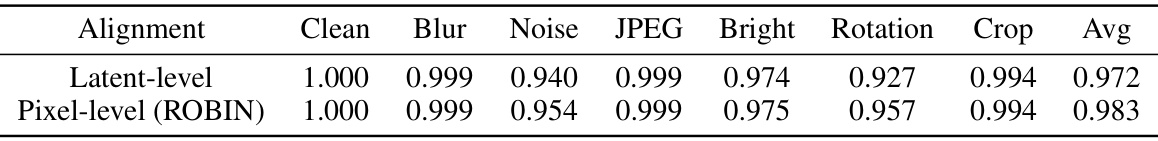
This table presents the Area Under the ROC Curve (AUC) for watermark verification under different image manipulations (Blur, Noise, JPEG, Bright, Rotation, Crop) for two watermarking approaches: latent-level and pixel-level (ROBIN). The ‘Clean’ column shows the AUC for unmanipulated images. The results indicate the robustness of the ROBIN method against various image distortions, particularly in comparison to the latent-level method.
Full paper#